
26 Oct Financial Services: IT Security & Cyber Protection in Banks from Malware and More

Malware is on the march with attacks rising emphatically across the financial sector in 2018. Causing tension in financial industry IT departments since a breach successfully hoodwinked a Spanish bank in a $1 billion haul earlier this year.
Fears of attacks are well warranted in the banking community but often not heeded by senior management outside of IT – IBM X-force reports that over the past two years the financial sector has been the most attacked industry, representing 17% of verified attacks and 27% of security incidents across industries.
Banking Trojans:
Attacks on the financial sector are not exactly surprising, it’s one way that attackers can win big and a large portion of the cybercrime fraud haul is down to Banking Trojans exclusively. Banking Trojans are nothing new, but the detail and their capabilities are increasingly menacing. The new Trojan strains are made up of sophisticated source-code that would not be utilized by fly-by-night solo operators or even small teams. The attackers are also setting the bar much higher in terms of targets and larceny capability, indicating organized crime gangs are now distributing these Trojans along with other attacks.
Inevitably, the attacker’s core focus is on business targets – compromised business accounts are simply more profitable. The attackers appear undaunted by threats and international agreements to halt cybercrime, these large syndicates remain at large and unpunished, even while conducting large-scale infiltrations and attacks on internal systems. Emboldened by the lack of punishment the number of heists in 2015, 2016 and 2017 has increased. The numbers are already large with Industry experts expecting cyber-fraud to grow: with some forecasting losses of 2.1 trillion by just 2019. These eye-bulging numbers should force banking organizations to take note – organized crime gangs are coming.
How Do Attacks Occur:
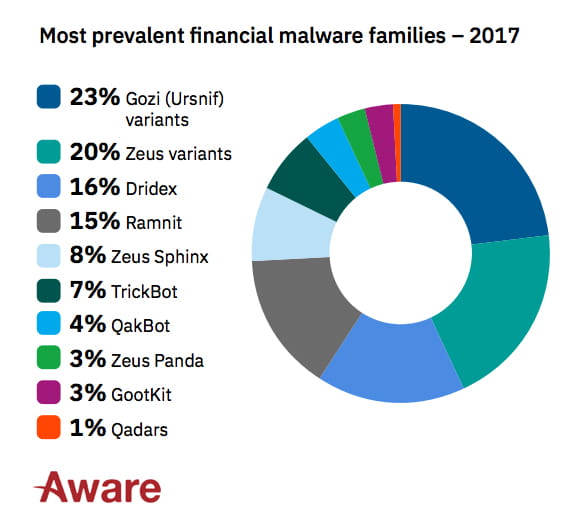
From IBM’s X-force report the number-one attack vector was injection attacks, which made up 79% of the sample, the most active malware in the sector was Gozi (Urnsif), that toppled Zeus from the top spot in 2017. Gozi makes up a remarkable 25% of all activity tracked, leading the field in Number of Campaigns, Code Updates, Reach and Attack volume. Once notorious financial Trojans Neverquest, GozNym, and Shifu have all declined significantly.
Losses due to cybercrime are a substantial and growing issue for financial institutions across the globe. Typically attackers are on the offensive with bank customers, using phishing techniques and credential stealing malware as well as code that can intercept online transactions. However, organized crime syndicates are also targeting the enterprise networks of banks. There have been many cases of breaches on financial institutions including the compromised web servers of a Polish financial regulator, a bank heist in Mexico and a breach of an Indian bank.
Attackers are adept at seeking out vulnerabilities through unpatched software and applications. One of the largest breaches in the US in 2017 was due to an unpatched web application which led to a data leak which impacted half the US population; 209,000 credit card details and personally identifiable information of 192,000 US consumers.
Aside from worming their way into through unpatched data vulnerabilities, attackers launched DDOS attacks against financial institutions impacting their business operation and disrupting their service. Lloyds fell victim to such an attack which left their customers unable to access their services for 2 days.
The attacks on financial institutions are relentless and they show no sign of slowing up. Standard protocol for any cyber security breach is made up of 3 core components: educate your staff, protect your business through software and processes, and backup your essential documents and applications.
We educate.
We update.
We protect.
We secure.
We back up.
You can learn more about Aware’s RMM solution here or contact our IT Security team.
- Microsoft Copilot vs ChatGPT: Navigating the Future of AI Assistants - April 3, 2024
- Harnessing Microsoft 365 Copilot for Educational Excellence - March 21, 2024
- How Can Microsoft Copilot Help Human Resources Staff? - March 20, 2024
- Microsoft Copilot for Human Resources - March 20, 2024
- The Business Benefits of Microsoft Copilot for Marketing Professionals - February 19, 2024
- The key business benefits of Microsoft Copilot - February 19, 2024
- How To Increase Your Employee’s Productivity with Copilot for Microsoft 365 Word - February 16, 2024
- Transform with AI – Journey with Aware - November 20, 2023
- What is Edge Computing? Advantages and Disadvantages: - May 20, 2022
- SAP Business One Vs Microsoft Dynamics 365 - November 12, 2021

