The Aware Blog
Our official blog with news, technology advice, and business culture.

From Sidekick to POS Hub: How Shopify Winter ’26 Rethinks Store Operations
Table of Contents Why Shopify Winter ’26 Feels Like a Shift in How Stores Operate In previous posts we have already outlined the strategic position

From Sidekick to POS Hub: How Shopify Winter ’26 Rethinks Store Operations
Table of Contents Why Shopify Winter ’26 Feels Like a Shift in How Stores Operate In previous posts we have already outlined the strategic position

What is Gamarue?
What is Gamarue? Gamarue is a particularly pernicious malware that has been prevalent worldwide but has exceptionally high encounter rates specifically in Asia. It
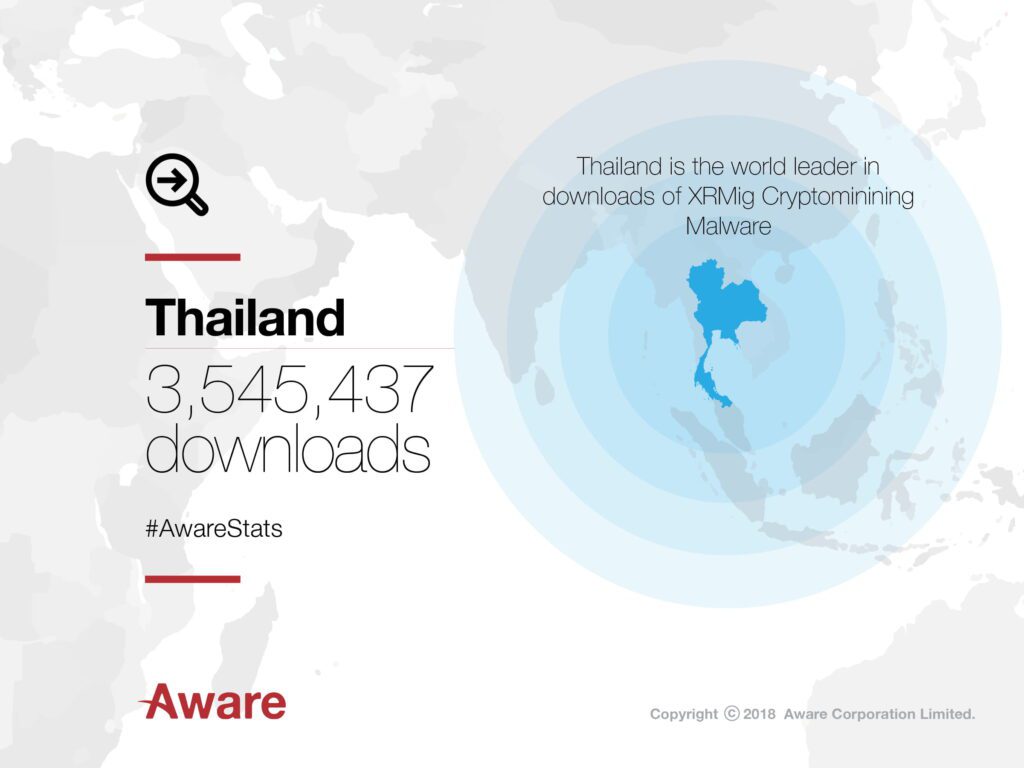
Malware Rates in Thailand
Malware in Thailand is on the rise, in the face of a damning new report from Microsoft Intelligence Security – we look at the numbers.

Top 10 Benefits of Veeam
Why Veeam? Why Now? Lightning-paced technological innovation waits for no man or business. The move towards virtualized environments is relentless and if you are

Why Your Business Needs HPE StoreOnce
A stalwart of Gartner’s Magic Quadrant in both 2014 and 2015 – HPE StoreOnce has been an industry leader in deduplication targeted backup appliances for

10 Actionable Methods to Improve your Security Posture
This page is also available in ไทย. Free Download: Click Here Protecting your business against cyber-attacks doesn’t need to be costly or complicated. In fact,

When the Storm Comes: Why You Need Business Continuity Planning
Business Continuity Planning (BCP), defines a process or system for recovering a business during and after a disaster. It is one of the most critical

What is Ransomware as a Service (RaaS)?
It’s boom time for Ransomware developers, a once in a generation shot at leveraging technological advances against defenseless people and businesses. Like an odious gold

The Father of Thai Technology
The Late King Bhumibol Adulyadej was so much more than a monarch, he was the man who shaped modern Thailand, a man of many roles;

The Sufficiency Economy Philosophy
Sufficiency Economy Philosophy (SEP), is a visionary and award-winning idea, attributed to the Late King Bhumibol Adulyadej. An economic and social model pieced together after
Let's Talk Solutions
Don’t face obstacles alone – tell us about your needs. We’ll listen, suggest options, and together build technology to accomplish your goals.
Guaranteed Follow-Up — Within One Business Day
- Email us or fill out the form
- Connect with our English-speaking team
No chasing. No hassle. It’s easy.