23 Apr REFLECTED CROSS-SITE SCRIPTING – THE EASIEST WAY TO DISCOVER VULNERABILITY
Cross-Site Scripting (XSS) is a security weakness (Vulnerability) that takes advantage of dynamically generated Web pages. In an XSS attack, a malicious client-side script is embedded into a legitimate Web request. The script is activated when an unsuspecting Web browser later reads it. It manipulates those Web applications that have not protected themselves against XSS.
There are two main types of XSS:
- Stored Cross Site Scripting
- Reflected Cross Site Scripting
Stored Cross Site Scripting
Malicious script code is stored in the database. It gets executed when a user requests the page or data.
Reflected Cross Site Scripting
Malicious script gets executed if there is no validation at the server end.
Common targeted objects for reflected cross-site scripting are:
- Search text box’s
- Any Parameter in the URL string
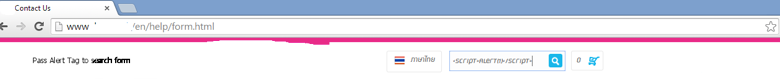
Example 1 – Using Search Textbox
- Open a website with a search box
- Enter basic javascript code <script>alert(‘XSSed’)</script>
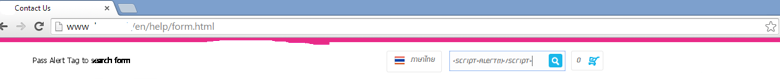
3. Click Search
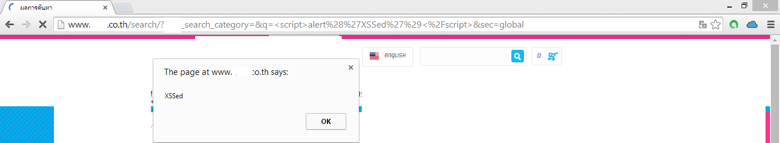
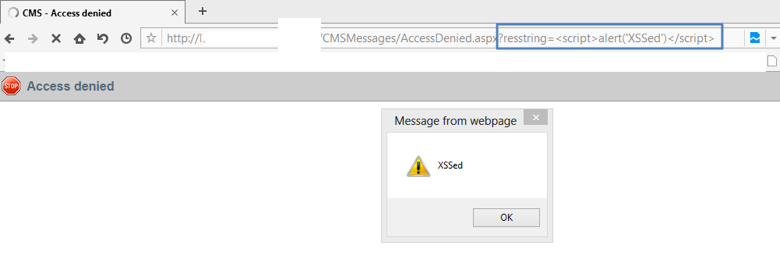
Example 2 – Using URL Parameter
- Open any webpage with parameters in URL string (in our case it is restring)
- Replace parameter value with basic script code
- Reload URL
Countermeasures
To avoid an XSS attack, implement code into your Web application that block certain command tags and trigger script events in HTML, such as the greater than (>) and less than (<) symbols, the ampersand (&), double quotes (“”), and carriage returns.
- WHAT THE CEO IS READING – IMPROVING THE BUSINESS-TO-BUSINESS CUSTOMER EXPERIENCE - March 26, 2016
- WHAT THE CEO IS READING – LEADING AND GOVERNING THE CUSTOMER-CENTRIC ORGANIZATION - March 22, 2016
- Spreading The Love In The Office For Valentines Day - March 2, 2016
- WHAT THE CEO IS READING – MANAGE YOUR EMOTIONAL CULTURE - February 23, 2016
- WHAT THE CEO IS READING – GETTING TO SI, JA, OUI, HAI, AND DA - December 9, 2015
- Aware presents at the “Creativity Connect Forum” - December 1, 2015
- Aware’s Annual Community Care Event 2015 - November 24, 2015
- Aware Will Be Presenting at the International Creativity Forum, ‘Creativity Connect’ - October 28, 2015
- Aware Wins Esri & ICMA Social Services App Challenge with ‘The Raccoon Challenge’ - October 5, 2015
- 2 นาทีข่าวเทคโนโลยีประจำเดือนกันยายน - October 2, 2015
